Proactive Security at PRISMA

At PRISMA, we place great value on driving positive change by constantly evolving our product and services. However, given the sensitive nature of our platform and the data it holds, it’s also critical that any changes we implement are done so safely and securely. And central to our efforts to maximise security is the conducting of regular external security assessments.
The origins of "pen-testing"
Back in 1965, one of the first IT security conferences took place in the United States, attended by several of the field’s leading computer security experts. During the conference, it was noted that one of the host’s employees had been able to easily undermine various system safeguards deployed for the event
It was this incident that led to the first formal requests to use computer penetration as a tool for studying system security. Today, more than 50 years later, penetration testing - or ‘pen-testing’ to use its abbreviated name - has become a common tool for performing security assessments across industries.
What exactly is a penetration test?
If you’ve seen the movie Ocean’s 11, you may already have some idea of what a pen-test is.
Let’s imagine you’re casino owners and have hired Danny Ocean, the film’s protagonist, to test how easy it would be to access your vault. In this hypothetical situation, Danny would be your penetration tester, and the vault would be your informatics system.
When performing a penetration test, you’re hiring an external party to try to gain unauthorised access to your systems and data by replicating the methods that hypothetical threat actors would likely use.
Our attack model, and the importance of reporting
There are several ways of conducting a penetration test. As part of this introductory article, we’d like to provide some insight into the specific testing methods we choose to use at PRISMA.
To kick things off, let’s take a look at our use of the ‘attack’ model that was inspired by the methods of James P. Anderson, a pioneer of information security, back in the 1970s.
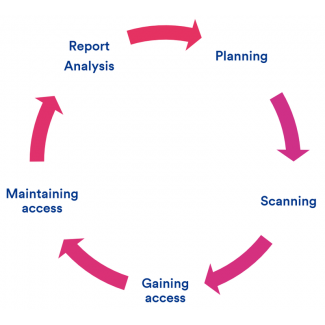
Our penetration test attack model comprises 5 stages:
- Planning
Preparing the plan of attack. In this initial phase a pen-tester lays out the methods they’ll use in attempting to breach a system.
- Scanning
The tester performs scans of networks and applications, looking for a weak point where they can gain access to the system.
- Gaining access
The tester proceeds to gain access.
- Maintaining access
After successfully gaining access, the tester attempts to install a “backdoor” that will allow them access again in the future.
- Reporting
The tester creates a report outlining their findings. Companies can then use this report to enhance their security and shore up any weak points in their systems identified during the pen-test.
How we use reports to improve security
No matter how critical the findings of a pen-test, the report provides an invaluable appraisal of a company’s security. It will identify where the company needs to improve, as well as what it’s already doing well.
Going beyond technical information
A comprehensive pen-test report should include information on both the technical and business aspects of your service.
To ensure our pen-testers are equipped to provide this information, prior to them conducting a pen test we take the time to work closely with them, familiarising them with both the technical aspects of our company and the intricacies of its business operations.
During this preparatory phase, we take them through the main processes involved in using our services. This is because the more they know, the better equipped they’ll be to breach our security during testing - and the more ways they try to breach our security, the more comprehensive and insightful the subsequent report is likely to be
In contrast to this collaborative approach, an ‘off-the-shelf’ pen-test simply couldn’t result in the same depth of insight.
How can we get even more out of a pen-test?
As well as being a crucial method for gaining real-world evaluations of your company’s security processes, penetration testing can also be a useful tool for training exercises for your information security team.
There are several different approaches to using pen-testing as a training exercise. At PRISMA we currently use two types of testing for this purpose:
· Blind Tests: For blind tests, we don’t tell our team in advance that a test is going to be conducted. This means that when they detect a problem, they remain unaware that it’s just a test, better reflecting a real-time situation and allowing us to more accurately monitor their response to it. Once they’ve detected a system breach, we then reveal that it was merely a drill.
· Forensic Exercise: The testing we most often employ are forensic exercises. For these, we inform our security team that a test will take place, and then investigate the findings in a forensic manner in order to detect patterns and correlations of relevance.
Once the tester has submitted their report, we then estimate what the results will be prior to reading it. To do so we systematically analyse our logs to understand what the first indicators of a breach are. Though it may seem like we’re consulting a magic ball for answers, we’ve found this approach has allowed us to hone our own investigative skills and improve our monitoring capacities.
In short, penetration testing reveals things to us that we cannot otherwise see and has become an invaluable tool for improving security at PRISMA.
